Choosing Your Modern Sign In Solution
A modern sign in solution is more than a username and password field; it's a strategic asset that secures the digital front door to your business. The right solution strikes a perfect balance between rock-solid security and an effortless user experience, ultimately protecting your data and boosting productivity.
What Is a Modern Sign In Solution Anyway?
Imagine your company's digital resources are rooms in an office building. A traditional sign-in process forces every employee to carry a massive keychain with a different key for every door. It's not just inefficient; it's a major security risk. A staggering 81% of data breaches trace back to weak or stolen passwords, a problem that multiplies with every new application you add.
A modern sign in solution acts like a smart concierge for this building. Instead of juggling dozens of keys, users get one master key that grants them authorized access. This simple switch dramatically boosts both security and day-to-day productivity.
The Power of a Unified Entry Point
At the heart of a modern sign in solution is Single Sign-On (SSO). This technology allows a user to log in once with a single set of credentials to access multiple applications, delivering immediate benefits.
By centralizing the login process, a modern sign in solution provides significant advantages:
- Reduced Password Fatigue: With fewer complex passwords to remember, employees are less likely to write them on sticky notes or reuse weak credentials across multiple platforms.
- Enhanced Security Posture: A smaller number of passwords shrinks the attack surface for cybercriminals, making it easier to enforce stronger, consistent security policies.
- Improved User Productivity: Eliminating the need to repeatedly log into different systems saves valuable time, allowing your teams to focus on core tasks instead of password management.
More Than Just Access, It’s About Control
Modern systems offer sophisticated control over how users gain access. A key component is Multi-Factor Authentication (MFA), which adds a crucial second layer of defense. By requiring at least two verification factors, MFA makes it significantly harder for unauthorized individuals to compromise an account.
A robust sign in solution is the foundation of a modern security strategy. It transforms access management from a necessary hassle into a powerful tool for protecting data, ensuring compliance, and empowering users.
These principles extend beyond digital access to manage contractors, partners, and physical visitors. The connection between digital and physical security is clear, as explored in our guide on what is a visitor management system. The goal remains the same: create a secure, efficient, and welcoming environment for everyone, whether they're online or on-site.
Core Benefits of a Better Sign In Experience

Adopting a modern sign in solution is a strategic move that enhances productivity, security, and team morale. It transforms the daily login chore from a point of friction into a smooth, secure gateway to getting work done.
This shift delivers a massive benefit to your IT support teams. Password-related issues are a notorious time sink, accounting for an estimated 20-50% of all IT help desk calls. Implementing a unified sign-in solution drastically slashes these repetitive tickets. This frees up skilled IT professionals to focus on strategic projects that drive business growth, rather than spending their days on password resets.
Boosting Team Productivity and Morale
A clunky login process is a constant drag on productivity. Every minute an employee spends recalling a password, getting locked out, or waiting for a reset is a minute lost. Across an entire organization, these small delays accumulate into significant productivity losses.
A better sign-in experience gives that time back. With a single, secure entry point, employees can access their tools faster and with less frustration. This not only boosts output but also improves the workday experience and lifts morale by removing a common headache. This is one of the many benefits a modern visitor management system delivers, streamlining everything from the front lobby to every digital touchpoint.
The ultimate goal is to make security invisible and access effortless. When employees don't have to think about passwords, they can focus on what they do best. That creates a more productive and positive place to work.
Gaining Centralized Security Oversight
Perhaps the most critical benefit is the complete visibility a modern sign in solution provides. Instead of managing access across dozens of separate apps, you gain a single, centralized dashboard. This bird's-eye view is a game-changer for security and compliance.
From one location, administrators can enforce consistent security policies, monitor access patterns in real-time, and quickly spot suspicious activity. If a threat emerges, they can revoke access to all connected systems instantly with a single click, containing a potential breach before it escalates.
This centralized control simplifies key cybersecurity functions:
- Uniform Policy Enforcement: Apply strong password rules and multi-factor authentication across every application simultaneously.
- Simplified Auditing: Easily generate comprehensive access logs for compliance reports, demonstrating who accessed what, and when.
- Rapid Response: Immediately disable access for departing employees, closing a common and high-risk security vulnerability.
This level of control is crucial as businesses increase their reliance on cloud services. The global single sign-on (SSO) market is projected to grow by a compound annual growth rate (CAGR) of 22% by 2030 as companies work to manage user access and combat "password fatigue."
Ultimately, a modern solution builds a stronger, more efficient, and more secure foundation that protects your company's reputation and bottom line.
Key Components of an Effective Sign In Solution
To understand what makes a modern sign in solution effective, we need to look at its core components. These are the engines that drive security, boost productivity, and create a seamless user experience. When these parts work in harmony, they create a digital front door that’s both incredibly secure and easy to use.
This graphic breaks down the main ways modern systems handle user access.
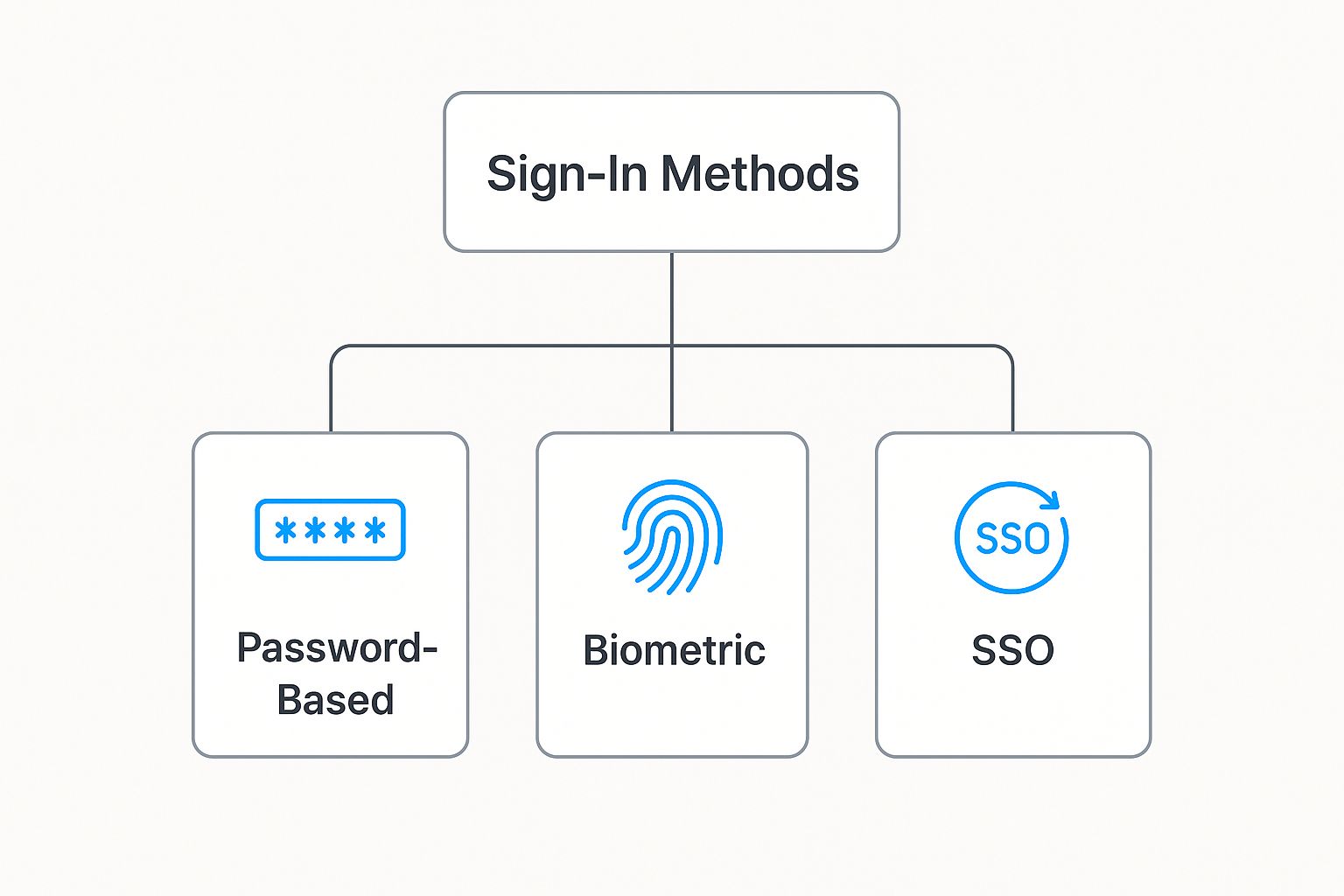
The best approaches move far beyond simple passwords, incorporating more secure and user-friendly methods like SSO and biometrics.
Single Sign-On: The Productivity Booster
If one component has a massive impact on daily work, it's Single Sign-On (SSO). As a master keycard for your digital world, SSO lets employees log in once to access everything they need, eliminating the need to juggle dozens of different passwords.
This single change dramatically improves efficiency. It ends the frustrating cycle of logging in and out of tools all day, giving your team valuable time back. It also drastically reduces password-related help desk tickets, freeing up IT staff to focus on more strategic initiatives.
Multi-Factor Authentication: The Digital Bodyguard
While SSO simplifies access, Multi-Factor Authentication (MFA) ensures it remains secure. If a password is the lock on your door, MFA is the security guard demanding a second piece of ID. It provides a powerful shield against unauthorized access.
MFA works by requiring users to provide at least two forms of proof to verify their identity. This typically combines something you know (a password), something you have (a code from your phone), and sometimes something you are (a fingerprint). This layered security is incredibly effective. Even if a cybercriminal steals a password, they are stopped cold without the second factor. In fact, MFA can prevent over 99.9% of account compromise attacks.
The combination of SSO and MFA strikes the perfect balance for any modern workplace. SSO delivers the speed and convenience people want, while MFA provides the tough security the business needs.
Adaptive Authentication: The Smart Sentry
Adaptive authentication adds a layer of intelligence, acting like a smart security system that adjusts its defenses in real-time. Instead of treating every login identically, it analyzes risk signals to determine if additional verification is needed.
For instance, an employee logging in from the office during business hours may gain access seamlessly. However, if the same account attempts to log in from an unrecognized country at 3 AM, the system flags the risk. It then "steps-up" security, perhaps by requiring an MFA code or blocking the attempt altogether.
This risk-based approach delivers significant benefits:
- Less Hassle for Users: It avoids bothering low-risk users with unnecessary security hurdles.
- Smarter Security: It focuses security checks where they are most needed, responding to threats as they emerge.
- Proactive Defense: It identifies and blocks suspicious login attempts before they escalate into security incidents.
The demand for such robust security is driving massive market growth. The global authentication market is projected to jump from USD 22.8 billion in 2025 to USD 98.6 billion by 2035. This huge increase is fueled by rising cyber threats and the critical need for secure digital access. You can find out more about the authentication market forecast to see how vital these components are becoming.
Modern vs. Traditional Sign In Methods
The benefits become clear when comparing old methods with a modern approach. The difference in security and user experience is night and day.
| Aspect | Traditional Method (Password Only) | Modern Sign In Solution (SSO & MFA) |
|---|---|---|
| User Experience | Frustrating. Users must remember dozens of unique passwords, leading to password fatigue and frequent resets. | Seamless. Users log in once to access all their applications, eliminating the need to manage multiple passwords. |
| Security Level | Low. Highly vulnerable to phishing, brute-force attacks, and credential stuffing. A single stolen password can compromise an account. | High. MFA adds multiple layers of defense, making it nearly impossible for attackers to gain access even with a stolen password. |
| IT Burden | High. IT teams spend significant time on password-related help desk tickets and managing user access for each application individually. | Low. Centralized access management and fewer password resets dramatically reduce the administrative workload on IT staff. |
| Productivity | Reduced. Time is wasted logging in and out of different systems and dealing with forgotten passwords. | Increased. Quick, frictionless access to necessary tools means employees can get to work faster and stay focused. |
Sticking with outdated password-only systems is like using a simple padlock in an age of high-tech security threats. Modern solutions provide the comprehensive protection and efficiency that today's businesses demand.
Enhancing Security and Ensuring Compliance

For most businesses, the discussion around a new sign-in solution centers on two critical goals: strengthening security and simplifying compliance. Relying on an outdated access system is like leaving your back door unlocked. A modern solution offers genuine peace of mind by actively protecting your most critical digital assets.
This proactive security is essential. The average cost of a data breach has now reached a staggering $4.45 million. A solid sign-in solution acts as your first line of defense, helping you avoid these catastrophic financial and reputational damages.
Centralized Control for Airtight Security
Managing user access across dozens of apps without a single system is chaotic. A modern sign-in solution replaces that chaos with one powerful control panel, which is a game-changer for security. From a single dashboard, you can see exactly who is accessing your systems, from where, and when. This visibility allows you to apply consistent security rules across the board, plugging previously unknown vulnerabilities. This is a core principle for enhancing workplace security with a visitor sign in system, as effective oversight is key to both physical and digital safety.
A major benefit is automated de-provisioning. When an employee or contractor leaves, you can revoke their access to every connected application instantly with a single click. This simple action closes one of the most common and dangerous security gaps, ensuring former team members cannot retain digital access.
Making Compliance Audits Effortless
Preparing for a compliance audit under regulations like GDPR, HIPAA, or SOC 2 can be a nightmare with a fragmented access system. Auditors require clear, documented proof of who accessed specific data and when. Piecing this information together manually is time-consuming and prone to errors.
A modern sign-in solution transforms this ordeal. It automatically generates detailed, timestamped audit trails for every login attempt and stores them in one central, searchable location.
When an auditor comes knocking and asks for access records, you can pull a complete report in minutes, not weeks. This capability shifts compliance from a massive operational burden to just another manageable process.
These audit trails are also a valuable internal security tool. By monitoring access patterns, your team can quickly spot unusual behavior that might signal a compromised account or an insider threat, enabling an immediate response.
Proactive Protection Against Emerging Threats
Cybercriminals are constantly developing new attack methods. Relying on a simple password is no longer sufficient. A proper sign-in solution provides the layered defenses needed to stay ahead of threats.
Implementing strong measures like Multi-Factor Authentication (MFA) builds a formidable barrier against the most common attacks. Studies confirm that MFA can block over 99.9% of account compromise attacks, effectively neutralizing threats that rely on stolen passwords. This proactive stance shifts your security posture from reactive to preventative. Instead of cleaning up after a breach, you are actively stopping unauthorized access from happening in the first place. This protects not only your data but also your company’s reputation and customer trust.
How to Choose the Right Sign In Solution
Selecting the right sign in solution is a critical decision that impacts security, productivity, and your budget. It's about finding a partner that fits your business—secure, scalable, and simple to manage. The process begins with a clear assessment of your actual needs.
It's easy to be impressed by features you'll never use. The best approach is to focus on the fundamentals of where your business is today and where it is headed.
Define Your Core Requirements
Before evaluating vendors, create a clear picture of your IT environment. Does your company operate primarily in the cloud with platforms like Salesforce or Microsoft 365? Or do you rely on a mix of modern cloud apps and legacy on-premise systems?
Your answers will immediately narrow the field. A solution designed for cloud apps might not support your custom-built legacy software. The first step is to list all your essential applications.
Choosing a sign in solution is like drafting a blueprint before building a house. You must define the foundation—your core applications and user base—before you can select the right materials and tools for the job.
Once you know what you need to protect, you can create a checklist to compare different options fairly and make an informed decision.
Create Your Evaluation Checklist
A structured approach ensures you don't miss crucial details. As you engage with potential vendors, evaluate each one against the same standards to see beyond the sales pitch.
Key items for your checklist include:
- Integration Capabilities: A vendor with a large library of pre-built connectors for popular apps will simplify implementation. Ensure it also supports standards like SAML and OpenID Connect for custom or older systems.
- Scalability and Future-Proofing: Your sign-in solution should support your growth. Analyze the pricing model to ensure it won't become cost-prohibitive as you add users or applications.
- Vendor Support and Reputation: When a critical system has an issue, you need fast, effective support. Investigate the vendor's support options and read customer reviews to gauge their responsiveness and helpfulness.
Think Beyond the Initial Price Tag
The upfront cost is only part of the story. The true value of a sign in solution lies in its total cost of ownership (TCO) and the return on investment (ROI) it delivers over time. For a deeper look at this, our guide on how to choose the right visitor management system for your business covers similar ideas about finding long-term value.
Consider the hidden savings, such as the IT time saved from fewer password resets and the immense cost of preventing even a single data breach. The digital signature market alone, valued at USD 8.65 billion in 2024, is projected to hit USD 238.42 billion by 2034, highlighting the explosive growth in secure identity tools. You can discover more insights about the digital signature market on Precedence Research.
By taking this bigger-picture view, you can make a choice you’ll be happy with for years, knowing it truly aligns with your business and security goals.
Common Questions About Sign In Solutions
Exploring access management often brings up practical questions about implementation, functionality, and overall impact. Let's address some of the most common questions to help you move forward with confidence.
Getting clear answers ensures your investment not only strengthens security but also aligns with your operational needs, delivering the smooth and safe access your teams require.
What Is the Difference Between a Sign In Solution and Identity Management?
This is an excellent question as the two are closely related but serve different functions. Think of it like the security system for a corporate building.
A sign in solution is like the high-tech security desk at the front door. Its primary job is authentication—verifying you are who you say you are using tools like Single Sign-On (SSO) and Multi-Factor Authentication (MFA). Its focus is securing that single point of entry.
Identity and Access Management (IAM), on the other hand, is the entire security operation for the whole building. It encompasses:
- Creating User Profiles: Issuing employee ID badges with specific information.
- Authorization: Deciding which floors and rooms each ID badge can unlock.
- Lifecycle Management: Activating a new employee's badge on day one and deactivating it upon their departure.
- Auditing: Keeping a detailed log of every door that was opened, by whom, and when.
In short, your sign in solution is a crucial, user-facing component of a much broader IAM strategy.
How Difficult Is It to Implement a New Sign In Solution?
The implementation process is often much smoother than people anticipate, especially with modern cloud-based systems. The complexity largely depends on your company's existing technology stack.
For businesses using popular apps like Google Workspace, Microsoft 365, or Salesforce, the process can be surprisingly fast. Leading providers offer extensive libraries of pre-built connectors that can be configured in minutes using guided wizards.
If your operations include custom-built or on-premise legacy systems, the integration will be more involved. In these cases, you will need a solution that supports open standards like SAML or OpenID Connect.
A huge factor in a successful rollout isn't just the tech itself, but the quality of the vendor's support. Look for a partner with clear documentation, responsive technical help, and a proven implementation plan to guide you. A good partner can turn a potentially complex project into a totally manageable one.
Can a Modern Sign In Solution Stop All Data Breaches?
While no single tool can offer a 100% guarantee against every threat, a modern sign in solution is arguably the most effective defense you can deploy. It directly addresses the leading cause of data breaches: compromised credentials.
Industry data consistently shows that a massive portion of cyberattacks—often cited as over 80%—begin with a weak, stolen, or reused password. By fundamentally changing how users access your systems, you neutralize this enormous threat.
Here’s how it dramatically reduces your risk:
- Eliminating Weak Passwords: With SSO, your team has fewer passwords to remember, making it easier to enforce the use of one strong, unique password for their main login.
- Blocking Credential Theft: MFA is the real hero here. Even if an attacker steals a password, they are stopped without the second factor from a user's device. This single layer is proven to block over 99.9% of automated password-stealing attacks.
- Providing Visibility: Centralized access logs allow you to spot and react to suspicious login attempts in real-time, enabling you to shut down an attack before it escalates.
While not a silver bullet, a robust sign in solution is like installing a high-security vault door on your digital office. It makes it exponentially harder for attackers to get in by shutting down their most common entry points.
Ready to secure your workplace and streamline your check-in process? The VisitUs platform offers a powerful, intuitive solution for managing visitors, contractors, and staff with ease. Learn more and see how VisitUs can transform your front desk.