What Is Two Factor Authentication Explained
Two-factor authentication (2FA) is a security process requiring you to provide two different authentication factors to verify your identity. Think of it as a double-check for your accounts. Your password unlocks the first door, but a unique, second key—sent only to you—is needed to get all the way inside. This simple second layer delivers a massive security benefit by making it much harder for unauthorized users to gain access.
Why A Single Password Is Not Enough
In today's digital world, a password alone is no longer sufficient protection. Data breaches are a constant threat, and with each one, millions of stolen usernames and passwords land online. This means that even a strong, complex password can be compromised, leaving it as the single point of failure between a hacker and your most sensitive information.
This is where two-factor authentication demonstrates its value. It creates a second, independent barrier—like your phone or fingerprint—that a criminal is highly unlikely to have. This simple action provides the crucial benefit of transforming vulnerable accounts into fortified digital assets.
"A password is like the lock on your front door. Two-factor authentication is like adding a deadbolt and a security guard who checks your ID before letting you in."
To put it simply, here’s a quick breakdown of what 2FA is all about.
Two Factor Authentication At A Glance
| Concept | Simple Explanation |
|---|---|
| What it is | A second security step after your password to prove it's really you. |
| Why it's needed | Passwords can be stolen, guessed, or leaked in data breaches. |
| How it works | Combines something you know (password) with something you have (phone) or something you are (fingerprint). |
| The Goal | To make it much harder for unauthorized people to access your accounts. |
This table shows just how straightforward the concept is, yet its impact on your security is massive.
The Power of a Second Layer
The benefit of adding this second step is immense. You elevate your security from a single, guessable secret to a multi-layered defense that is significantly harder to break. For any business, this enhanced security builds client trust and protects critical company data. This is a core benefit of modern security protocols, such as those found in a visitor management system, which safeguards physical premises with the same layered approach.
The statistics speak for themselves. Microsoft famously reported that enabling 2FA can block an incredible 99.9% of automated cyberattacks. Google’s own research found that adding a phone number for account recovery—a simple form of 2FA—can stop 100% of automated bots. You can see more data on how 2FA neutralizes common threats in these full two-factor authentication statistics.
This one simple action transforms your accounts from easy targets into fortified digital assets, providing significant peace of mind.
Why Your Password Is No Longer Enough Protection

Relying solely on a password is like using a simple screen door to protect a bank vault. For years it was standard practice, but today’s threats can bypass a password with alarming ease. Even a complex one remains a single point of failure.
The biggest problem is that password security is often out of your control. Massive data breaches are now commonplace, exposing millions of login details on the dark web. In fact, a shocking 81% of all hacking-related breaches are the result of stolen or weak passwords.
This means your carefully crafted password might already be for sale, through no fault of your own. This constant risk is why understanding what is two factor authentication is so critical. It adds a second, vital checkpoint that renders a stolen password useless to a thief.
The Rising Tide of Digital Threats
Beyond data breaches, cybercriminals use sophisticated phishing scams to trick people into revealing their login information. These fake emails and websites often look so convincing that even cautious users can be fooled.
The scale of this problem is staggering. It's estimated there are over 2,200 cyberattacks every single day, with a huge number aimed at stealing credentials. When a password is the only defense, you're always vulnerable.
A single stolen password can set off a domino effect, giving attackers access to all your other accounts if you reuse that same password. Adding a second factor stops this chain reaction dead in its tracks.
Securing Your Digital and Physical Front Door
This principle of multi-layered security is fundamental for any business. Protecting sensitive company and client information requires strong verification at every entry point. If you get locked out due to a suspected breach, you can learn how to reset your password and regain access securely.
A modern visitor management system provides the same benefit for physical spaces by verifying every person who enters a building. This creates a secure environment, ensures regulatory compliance, and builds trust—proving that a layered defense is always the best defense.
A Closer Look At The Different Types Of 2FA
Not all two-factor authentication methods offer the same level of security. They vary in protection and convenience, so understanding the options helps you choose the right one. Generally, 2FA methods fall into three categories based on what they require you to prove.
The goal is to create a layered defense by combining different types of proof to confirm your identity. The core idea is to pair something only you know with something only you have, or something that is uniquely you.
The Three Pillars of Authentication
The strength of two-factor authentication comes from mixing these verification types, making it incredibly difficult for an unauthorized person to access your accounts.
- Something You Know: This is your password or a PIN—a secret piece of information you have memorized.
- Something You Have: This refers to a physical object you possess, such as your smartphone (for receiving a code) or a dedicated hardware security key.
- Something You Are: This category is about biometrics, using your unique biological traits like your fingerprint or what is facial recognition technology to approve a login.
Mixing these factors is what provides the powerful security benefit of 2FA compared to relying on a password alone.
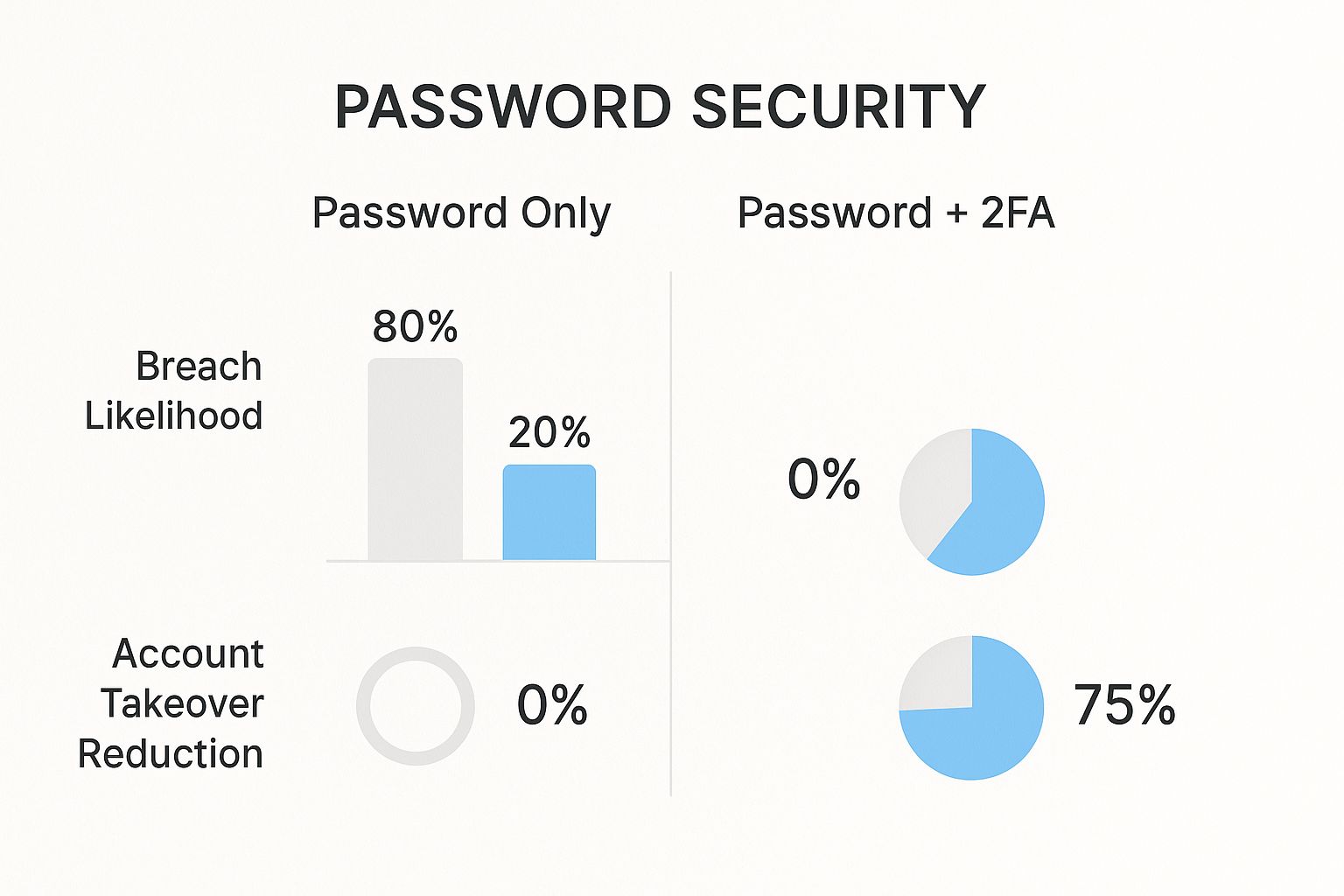
Adding that second factor drastically reduces the likelihood of a security breach, effectively shutting down account takeover attempts before they can start.
Common 2FA Methods and How They Compare
To help you understand the trade-offs, here are the most common 2FA methods, from least to most secure. Each offers different levels of protection and user-friendliness.
Comparison of Common 2FA Methods
| Method | How It Works | Pros | Cons |
|---|---|---|---|
| SMS & Email Codes | A one-time code is sent to your phone number or email address. | Widely available, easy to understand. | Least secure; can be intercepted by determined attackers. |
| Authenticator Apps | An app on your phone (like Google Authenticator) generates a fresh code every 30-60 seconds. | More secure than SMS, works offline. | Requires installing an app and initial setup. |
| Biometric Verification | Uses your fingerprint, face, or other unique biological trait to approve a login. | Very convenient and user-friendly. | Quality can vary by device; not all systems support it. |
| Hardware Security Keys | A small physical device (like a YubiKey) that you plug in or tap to authenticate. | The gold standard; virtually immune to phishing. | Costs money; you need to carry the key with you. |
Choosing the best method is a balance between the level of security you need and convenience. For most people, upgrading from SMS to an authenticator app provides a massive security benefit with little hassle. For protecting high-value accounts, a hardware key offers the ultimate peace of mind.
How 2FA Works In The Real World
Seeing two-factor authentication in action demonstrates how simple and powerful it is. The process is designed to be quick and intuitive, adding a critical security layer without slowing you down. It turns a major security threat into a minor, routine checkpoint.
The extra step you take when logging into your online bank is a perfect, everyday example of what is two factor authentication in practice. It unfolds in a few simple steps that prove you are who you say you are.
A Typical 2FA Login Flow
While the exact method can vary, the core steps are consistent, striking a balance between tight security and a smooth user experience.
- Enter Your Primary Credential: First, you type in your username and password on the login screen. This is your first factor, the classic "something you know."
- Receive a Secondary Prompt: The system then instantly sends a prompt to your trusted device, such as a text message with a six-digit code or a push notification from an authenticator app.
- Provide the Second Factor: You then enter the code or tap "Approve" on the notification. This proves you have your physical device—your second factor.
That’s it. Once the second step is complete, you’re in. The process takes just a few extra seconds but, as research shows, provides the benefit of blocking up to 99.9% of automated attacks.
This seamless verification provides the same benefit as a modern visitor management system: ensuring only authorized individuals can access a secure area, whether digital or physical. It confirms identity at the point of entry while keeping the experience smooth for legitimate users.
Setting Up Two-Factor Authentication On Your Accounts
Ready to secure your accounts? Enabling two-factor authentication is easier than you might think. While the layout varies between websites, the basic steps are nearly always the same. Getting started is a quick process that provides immediate peace of mind.
You'll almost always find the option in your account's "Security" or "Privacy" settings. Look for a heading like "Two-Factor Authentication," "2-Step Verification," or "Login Verification" to begin.
Choosing Your Preferred Method
During setup, you will be asked how you want to receive your second factor. You can choose between common methods like SMS text messages, an authenticator app, or a physical security key.
For most people, an authenticator app like Google Authenticator or Authy offers the perfect balance of security and convenience. They provide a significant security benefit over SMS and work even without a cell signal. For the highest level of protection, a physical key like a YubiKey is the best choice.
The market for these tools is well-established. RSA SecurID holds about 30.53% of the market share, with Yubico close behind at 22.49%, and Microsoft's Azure Multi-Factor Authentication at 18.95%.
After choosing your method, follow the on-screen instructions, which usually involve scanning a QR code or plugging in your hardware key. This is also a great time to review top credential management best practices to ensure all your accounts are secure.
Finally, the most critical step: save your backup codes. The service will provide a list of one-time-use codes. Store them somewhere incredibly safe, like a password manager or a physical safe, so you can still access your account if you lose your primary device. This process is a key part of maintaining secure access, and you can learn more in our guide on signing into a dashboard with multi-factor authentication.
Answering Your Questions About 2FA
It's normal to have questions when adopting a new security measure. Let's clarify some common points so you can feel confident making the switch.
Is 2FA Completely Foolproof?
While 2FA provides a massive security benefit, no single method is 100% perfect. It is designed to stop the vast majority of automated attacks—Google says it blocks nearly 100% of them—but a very determined attacker could still find a way through.
For example, a skilled thief might try to trick you into sharing your SMS code in a "man-in-the-middle" attack. This is why security experts recommend stronger methods like authenticator apps or hardware keys, which are far more resistant to these types of scams.
But for the average person, the benefit of turning on any form of 2FA is immense. It makes you a much harder target and is one of the most effective actions you can take to protect your accounts.
What Is The Difference Between 2FA And MFA?
This is a common question with a simple answer. Two-Factor Authentication (2FA) is a specific type of Multi-Factor Authentication (MFA).
Here’s the breakdown:
- 2FA always requires exactly two different factors (like a password plus a phone code).
- MFA is the broader term for using two or more factors.
So, all 2FA is MFA, but not all MFA is 2FA. A system requiring a password, a fingerprint scan, and a hardware key would be MFA (using three factors), but not 2FA.
What Happens If I Lose My Phone?
Losing your 2FA device doesn't mean you're locked out forever. When you first enable 2FA, you are almost always given a set of one-time backup codes.
It is absolutely crucial to save these codes somewhere safe, like a password manager or a physical safe. These codes are your emergency key, allowing you to regain access to your account and set up 2FA on a new device. As you adopt these security layers, it's also a good time to review mobile app security best practices to keep all your information protected.
At VisitUs, we build security into every interaction. Our visitor management system provides the benefit of robust verification, ensuring only the right people have access to your facilities for complete control and peace of mind. Learn more about how VisitUs secures your front desk.