What Is the Purpose of Physical Security Safeguards? Find Out Now
At its core, physical security is about creating layers of defense to protect your most valuable assets: your people, property, and information. Instead of a single wall, picture a modern fortress where deterrents, physical barriers, and active response plans work together to ensure a safe and secure environment.
Why Physical Security Is Your First Line of Defense
Physical security is the foundation of any comprehensive protection strategy. Before a cyber threat can even reach a server, a physical barrier must first be breached.
Effective safeguards are built on four key goals: to deter potential threats, detect breaches as they occur, delay intruders to provide valuable time, and enable a swift, coordinated response.
The importance of this field is backed by significant investment. The global physical security market, valued at USD 147.36 billion, is projected to grow to USD 216.43 billion by 2030. This growth isn't arbitrary; it reflects a serious organizational commitment to mitigating risks like theft, vandalism, and unauthorized access.
Expanding the Protective Perimeter
Today, the purpose of physical security extends far beyond preventing a simple break-in. Its benefits are crucial for:
- Ensuring Operational Continuity: Protecting critical infrastructure from damage preserves your business's ability to function without interruption.
- Safeguarding Sensitive Data: By controlling physical access to server rooms and file storage, you prevent insider threats and protect your most critical digital assets.
- Meeting Regulatory Compliance: Adhering to strict standards like HIPAA and GDPR, which require verifiable proof of who has physical access to sensitive information, becomes straightforward.
A modern visitor management system provides the benefit of being an intelligent gatekeeper, strengthening every layer of your security. Its true power lies in creating a live, auditable record of every person on-site, offering unparalleled oversight and control.
Let's break down the core purposes in more detail.
Core Purposes of Physical Security Safeguards
This table gives a quick snapshot of the "why" behind every lock, camera, and access card. It's about building a comprehensive shield that covers all your bases.
| Safeguard Purpose | Primary Benefit |
|---|---|
| Deterrence | Discourages potential intruders before they even attempt a breach. |
| Detection | Provides immediate alerts when a security event occurs. |
| Delay | Slows down an intruder, creating a critical window for response. |
| Response | Enables security teams to react quickly and effectively to an incident. |
| Access Control | Ensures only authorized individuals can enter specific areas. |
| Compliance | Creates an auditable trail to meet legal and regulatory requirements. |
Each of these functions is a piece of the puzzle, coming together to form a robust defense.
This approach transforms your front desk from a simple welcome point into an active security checkpoint, enhancing your team's awareness and control. To see how these elements fit into a broader strategy, you can explore our guide on physical access control systems.
The Four Pillars of an Effective Security Strategy
To truly understand physical security, it helps to see it as a single strategy built on four foundational pillars: Deterrence, Detection, Delay, and Response. These pillars work in harmony to create a resilient, multi-layered defense that keeps your people and property safe.
An effective strategy begins long before a threat reaches your door. The first layer is all about making potential intruders think twice.
Deterrence and Detection
Deterrence is about psychological prevention. Visual cues like prominent security cameras, clear warning signs, and a professional reception area all convey that your facility is a difficult target. Statistics show that well-protected businesses are far less likely to be targeted, effectively preventing incidents before they start.
Detection provides the massive benefit of immediate notification when a breach occurs. Alarms, motion sensors, and smart access control systems are designed to deliver real-time alerts, shifting your defense from passive to active.
This diagram breaks down how these different controls fit together to create a solid security posture.
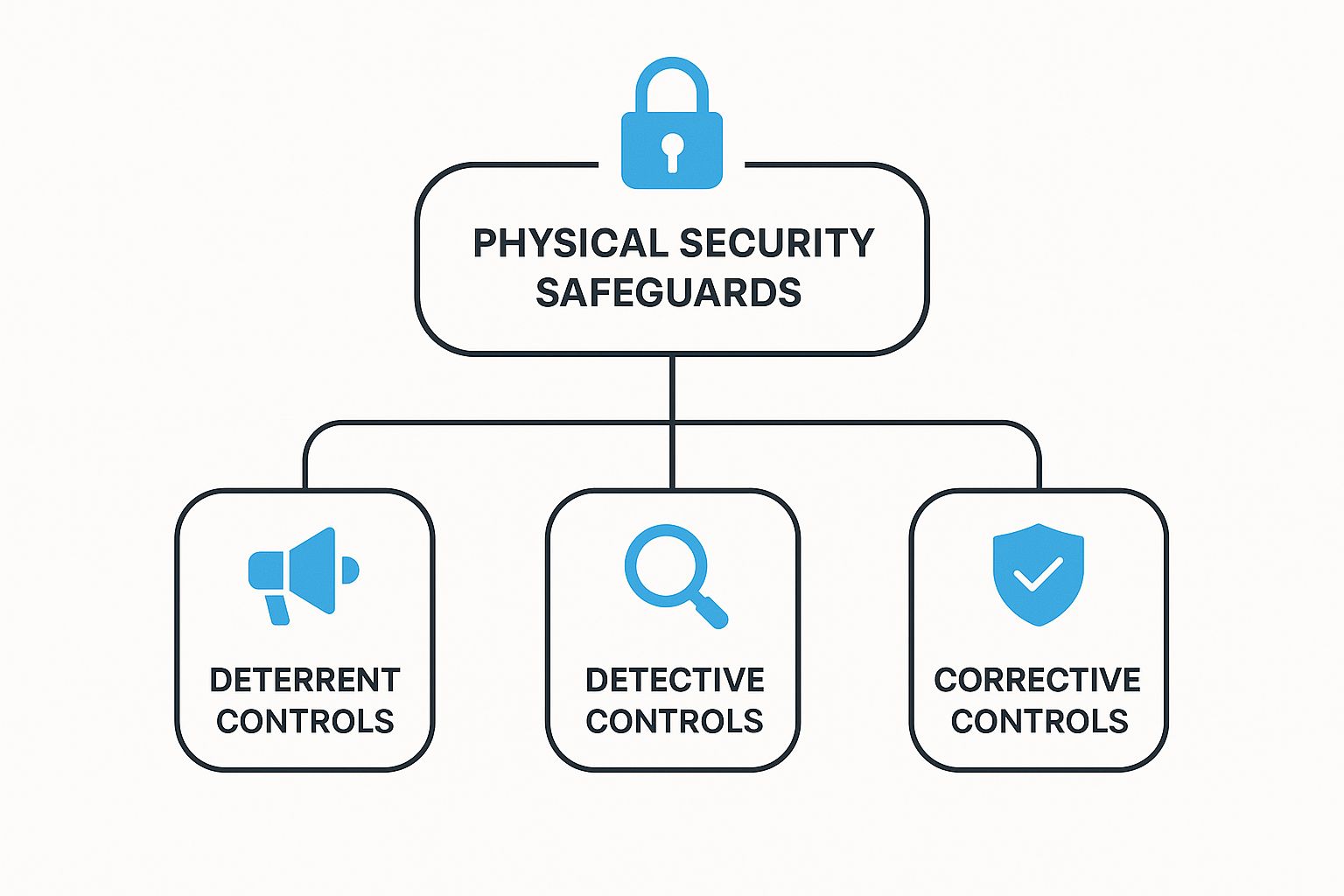
As you can see, a strong strategy needs a mix of proactive measures (deterrents), real-time alerts (detection), and reactive plans (response).
Delay and Response
If an intruder bypasses your deterrents, the next goal is to slow them down. This is the purpose of Delay tactics. Reinforced doors, high-security locks, and strategically placed barriers all create invaluable time for your team. Even a few extra minutes can be the difference between a minor incident and a major crisis.
That crucial time window leads directly to the final pillar: Response. This is the action plan that activates the moment a threat is detected. It involves coordinated procedures for security teams, clear staff evacuation routes, and direct communication with law enforcement, ensuring a controlled and effective reaction.
A modern visitor management system delivers the benefit of supporting all four pillars. It acts as a visible deterrent at your front door, instantly detects unauthorized entry attempts, and provides response teams with real-time data on who is in the building during an emergency.
For example, an automated check-in process not only denies entry to unauthorized individuals but also logs every attempt, instantly flagging suspicious activity for your security team. This integration strengthens every pillar, creating a smarter, more resilient defense. You can learn more about how a modern visitor management system for offices can become a cornerstone of this entire strategy.
How Common Safeguards Protect Your Business Operations
Understanding physical security theory is one thing, but seeing its practical value is where its importance truly clicks. The best safeguards are not just about locking a door; they create a smart, responsive environment that ensures your daily operations run smoothly and securely.

Among the most critical safeguards for managing access are modern access control systems. These tools directly address what is the purpose of physical security safeguards in any modern workplace.
Consider the risks of old-school keys: they can be lost, stolen, or copied, creating significant security gaps. It's a known fact that insider threats—whether malicious or accidental—are responsible for a substantial number of security breaches.
Modern solutions like biometric scanners or smart credentials eliminate these risks. By verifying that the person entering is exactly who they claim to be, you achieve a level of certainty that is essential for protecting high-stakes areas like server rooms or archives.
Unifying Security at the Front Door
While individual safeguards are effective, their true power is unlocked when they work together. A visitor management system acts as a central command post for your entrance, integrating separate security tools into one cohesive, intelligent ecosystem.
This integration delivers powerful benefits:
- Seamless Access Control: A pre-registered and approved visitor can receive automatic, temporary access to specific doors, eliminating manual work for your security team.
- Enhanced Situational Awareness: By linking surveillance cameras to your visitor log, security can receive an instant alert if an unknown person enters a restricted area.
- Effortless Auditing: Every entry and exit is logged digitally, creating a permanent, unchangeable record. This data is invaluable for security audits, incident investigations, and demonstrating regulatory compliance.
This connectivity transforms a random collection of devices into a truly cohesive security strategy. The result isn't just better protection—it's smoother operations and complete oversight.
Comparing Traditional vs Modern Access Control
Modernizing your physical security means rethinking outdated methods. A visitor management platform doesn't just replace the paper logbook; it enhances your existing access control, making it smarter and more efficient.
Here’s a quick breakdown of the benefits:
| Safeguard | Traditional Method (The Problem) | Modern Solution (The Benefit) |
|---|---|---|
| Visitor Verification | Relies on a receptionist's visual check or a paper logbook that can be easily faked. | Digital pre-registration, photo capture, and ID scanning confirm identity before arrival. |
| Access Provisioning | Manually issuing temporary keycards or keys, which can be lost, stolen, or forgotten. | Automated, temporary access credentials sent directly to a visitor’s phone for specific times and areas. |
| Activity Monitoring | No real-time tracking. You only know who was supposed to be there, not who actually is. | Live dashboard shows exactly who is on-site at all times, providing immediate situational awareness. |
| Record Keeping | Messy, insecure paper logs that are difficult to search and easy to tamper with. | Secure, searchable digital logs provide an instant, auditable trail for compliance and investigations. |
This shift from manual, reactive processes to automated, proactive ones is the core benefit. It tightens security while simultaneously reducing the administrative burden on your staff.
This integrated approach provides the benefit of a clear, bulletproof trail of every person who sets foot on your property. To see the full picture, learn more about the specific benefits of a visitor management system and how it turns your front desk into a strategic security asset.
Meeting Compliance Demands with Physical Security
While physical security is excellent for preventing theft or damage, a major driver for its implementation is meeting complex regulatory requirements.
Many businesses must adhere to strict standards like HIPAA, GDPR, and PCI DSS. For these organizations, failing to control access to sensitive areas isn't just a security lapse—it can result in staggering financial penalties and severe reputational damage.
Creating an Indisputable Audit Trail
Regulations demand verifiable proof of who can access servers, file cabinets, and sensitive workstations. Auditors are no longer just glancing at these controls; they are scrutinizing them. For example, proposed changes to the HIPAA Security Rule are making physical security a mandatory requirement.
This is where a modern visitor management system provides a significant benefit. It replaces messy paper logs with a permanent, digital, and instantly searchable record of every person who enters your facility.
When an auditor requests documentation, you can instantly pull detailed reports showing who was on-site, when they arrived, where they were authorized to go, and when they left. The ability to provide this definitive proof of access control is priceless.
A system that logs every entry and exit gives you the hard evidence needed to satisfy regulators and avoid hefty fines. It also provides vital data for sharpening your emergency evacuation procedures for the workplace, ensuring you can account for everyone in a crisis. This benefit turns a simple check-in into a powerful tool for both security and compliance.
The Future of Security is Proactive and Intelligent
The concept of physical security is evolving. For years, it was reactive—a lock was broken, an alarm was triggered. Today, that is no longer sufficient. The future is a smarter, more proactive strategy where potential threats are identified and neutralized before an incident occurs.

This shift is powered by technologies like artificial intelligence (AI) and the Internet of Things (IoT). Instead of merely reviewing security footage after a break-in, these systems can predict and prevent issues. The benefit is immense. In fact, 22% of organizations are already leveraging AI for improved threat detection, highlighting the rapid adoption of this trend.
From Reactive to Predictive Defense
Consider the capabilities of these smart systems. An AI-powered camera can detect unusual behavior, like someone lingering near a secure door, and instantly alert a guard. IoT sensors on that same door could detect a forced entry attempt and automatically lock down an entire section of a building.
This intelligence extends to other assets as well, such as vehicles protected by advanced vehicle immobilisers that offer a higher level of theft prevention.
A modern visitor management system is a cornerstone of this intelligent future. It provides the benefit of using data to automatically screen visitors against watchlists, automate access protocols, and integrate with smart building controls.
This is no longer just about standing guard. It's about creating a security posture that learns, adapts, and ensures you always remain one step ahead of potential threats.
Got questions about physical security? You're not alone. It's a topic that comes up a lot, and getting your head around the specifics is the best way to understand why these measures are so vital for protecting your people, property, and information.
Let's tackle some of the most common queries.
What Are the Three Main Types of Physical Security Safeguards?
Think of physical security as a defense with multiple layers. It's not just one thing, but a combination of efforts that work together. Generally, it breaks down into three core categories: access control, surveillance, and testing.
- Access Control: This is all about deciding who gets in and who stays out. It can be as simple as a security guard at the door or as high-tech as keycard systems and biometric scanners that read a fingerprint or face.
- Surveillance: This layer is for keeping an eye on things to discourage trouble and to have a record if something happens. We're talking about things like CCTV cameras and motion detectors.
- Testing: This one's easy to overlook but incredibly important. It's about making sure your systems actually work when you need them. Think fire drills, testing alarms, and running security breach simulations.
How Does Physical Security Impact Data Security?
The link between physical and data security is ironclad. You can have the best firewalls and encryption in the world, but they mean nothing if someone can just stroll into your server room and walk out with a piece of hardware.
A surprising number of data breaches have a physical element, like a stolen company laptop or someone gaining unauthorized access to a network closet.
A strong physical security posture is the first line of defense for your digital assets. By controlling who can physically touch your equipment, you prevent a major pathway for cyberattacks and safeguard sensitive information from being compromised.
Is a Visitor Management System a Physical Security Safeguard?
One hundred percent. A visitor management system is a cornerstone of any modern physical security strategy. It's a powerful tool that blends administrative and technical controls to create a smart, auditable security layer right at your front door.
While it doesn't physically bolt the door shut, it does something just as important: it verifies who people are, confirms they have a legitimate reason to be there, and creates a real-time log of every single person on-site. That data is priceless for day-to-day monitoring and is essential for proving compliance during an audit.
A robust visitor management system is key to a modern security strategy. See how VisitUs can provide the control, oversight, and peace of mind your organization needs by exploring our solutions.