Your Guide to Physical Access Control Systems
A physical access control system is the intelligent gatekeeper for your building, providing security and operational benefits that a simple lock and key cannot. Instead of a metal key that can be lost or copied—a problem that impacts an estimated 80% of businesses—these systems use credentials like ID cards or smartphones to manage who enters, where they can go, and when. This approach is a significant upgrade in both security and efficiency.
Understanding the Foundation of Modern Security
At its core, a physical access control system (PACS) manages the flow of people to ensure only authorized individuals access specific areas. It’s about creating an environment that is secure, efficiently managed, and fully auditable.
The demand for this control is surging, with the global market projected to grow from $10 billion to over $17.27 billion by 2029. This highlights a major shift as organizations move away from outdated security methods toward more intelligent solutions. You can explore the full market projections to understand the rapid growth in this sector.
A modern PACS provides instant, automated answers to three critical security questions for any access point:
- Who is trying to enter?
- Where are they authorized to go?
- When are they permitted access?
By automating these answers, a PACS removes the human error and guesswork inherent in manual security, providing a robust benefit for businesses seeking to protect people, assets, and information.
The Four Pillars of Access Control Systems
Every physical access control system is built on four core components that work together seamlessly. Think of it as a secure entry process: you need a "key" (credential), a device to read it (reader), a central brain to make the decision (controller), and a command center to manage it all (software).
These four pillars form the essential structure of any system.
| Component | Function | Example |
|---|---|---|
| Credential | The "key" that identifies a user. | ID card, key fob, mobile phone |
| Reader | Reads the credential and sends the information to the controller. | Card scanner, biometric sensor |
| Controller | The "brain" that makes the access decision based on pre-set rules. | A dedicated hardware panel |
| Software | The central dashboard for managing users, setting permissions, and viewing reports. | A web-based management platform |
Each component plays a distinct role, but all are interdependent for the system to function correctly.
This image illustrates how these components integrate into a single, cohesive system.
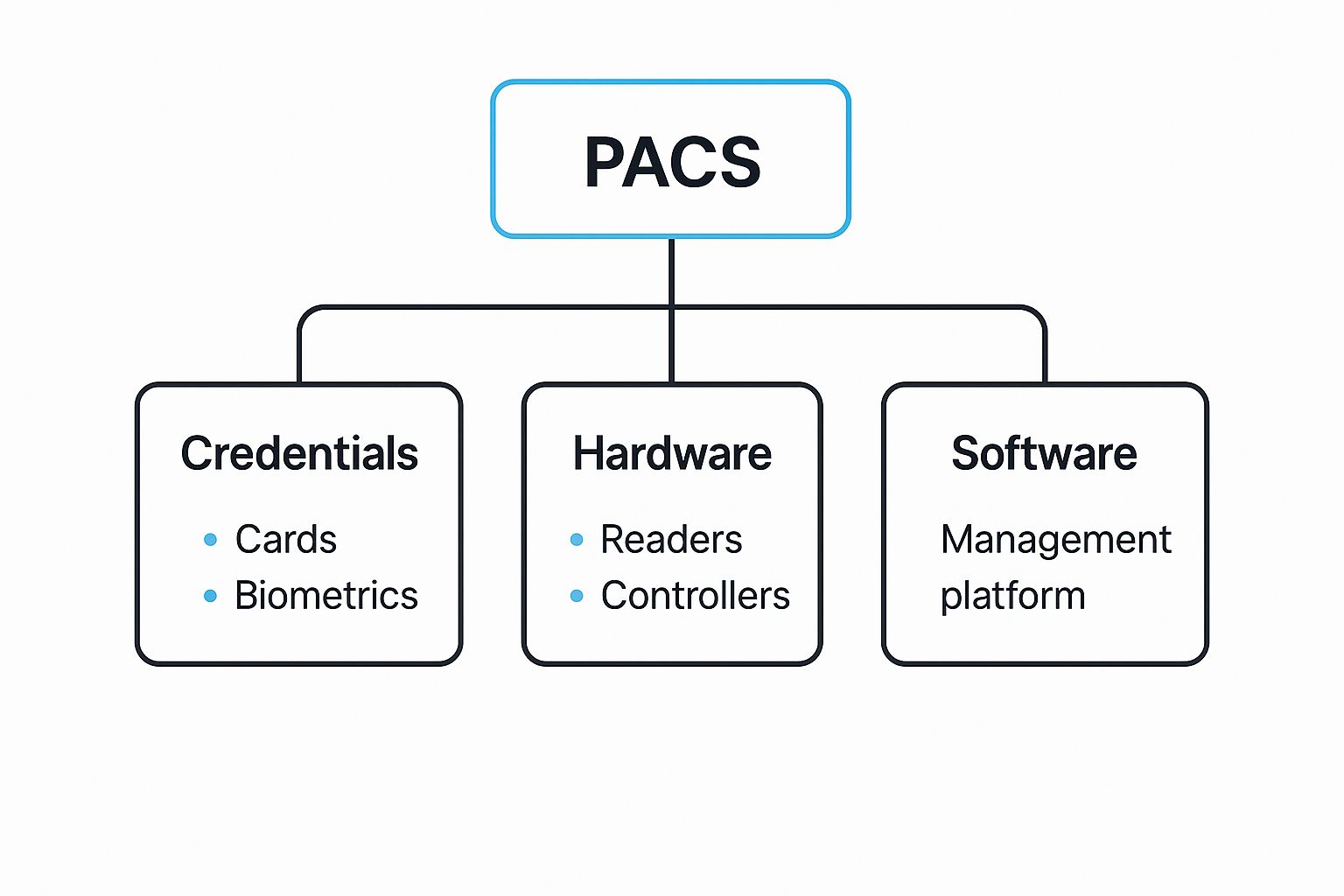
The seamless connection between a user's identity, the hardware at the door, and the central software is what makes the entire system effective.
A Closer Look at How It All Works
In a real-world scenario, an employee presents their credential—such as an ID card or smartphone—to a reader at a secured door. The reader instantly sends this data to the access controller.
The controller is the decision-making hub. It verifies the credential against its database and, in a fraction of a second, decides whether to grant or deny access based on your established rules.
If the credential is valid for that specific door and time, the controller signals the lock to open. If not, the door remains locked. The process is simple yet powerful.
Critically, every access attempt—successful or not—is logged in the software. This creates a permanent, searchable audit trail, a benefit that traditional lock-and-key systems cannot provide. This verifiable record is invaluable for security audits or investigating incidents.
Choosing the Right Access Credential Type

The "key" in a modern physical access control system has evolved significantly from the traditional metal key. Today’s credentials utilize various technologies, and choosing the right one means balancing security, user convenience, and budget. It's similar to securing a home: you might use a standard lock for the front door but a more advanced keypad or biometric scanner for a safe.
The Proven Reliability of Card-Based Systems
For decades, card-based systems have been the workhorse of access control. These plastic cards and key fobs offer a reliable, cost-effective way to manage access, especially for large numbers of people.
Card systems still command the largest market share due to their affordability and ease of use. However, the industry is increasingly adopting AI, biometrics, and multi-factor authentication (MFA) to address growing security demands. You can get more details on these trends by exploring the physical access control market.
The primary benefits of card systems include:
- Cost Efficiency: They are often the most affordable option per user, ideal for organizations with hundreds or thousands of employees.
- Ease of Management: Issuing a new card or deactivating a lost one is done with a simple click in the software, eliminating the need for locksmiths.
- User Familiarity: Most people have used a key card, so there is no training required.
The High Security of Biometric Credentials
When security is paramount, biometric credentials provide a level of protection that cards cannot match. By using a person's unique physical traits—like a fingerprint or face—to verify identity, biometrics make it nearly impossible for a credential to be lost, stolen, or shared.
A key card can be given to someone else, but a fingerprint cannot. This is why biometrics are the gold standard for protecting your most sensitive areas.
This type of access control is ideal for:
- Protecting Server Rooms: Ensuring only authorized IT staff can access critical infrastructure.
- Securing Research Labs: Safeguarding valuable intellectual property.
- Controlling Access to Financial Vaults: Adding a virtually unbreakable layer of identity verification.
Fingerprint scanners and facial recognition are common biometric tools, offering touch-to-enter and hands-free access, respectively. While the initial cost is higher, the peace of mind for high-value assets is a significant benefit.
The Unmatched Convenience of Mobile Credentials
The latest evolution in access control places the credential on a device people already carry: their smartphone. Mobile credentials turn an employee's phone into a secure access pass, offering a major benefit in convenience and operational efficiency.
This approach eliminates physical cards. For employees, it's one less item to carry and lose. For administrators, it means credentials can be issued or revoked instantly and remotely. A new hire can receive access rights before their first day, and a departing employee's access can be terminated the moment they leave. This blend of security and convenience is why mobile access is becoming the new standard for forward-thinking businesses.
What Are the Real Benefits of Modern Access Control?

A modern physical access control system offers benefits far beyond unlocking doors. It transforms your security from reactive to proactive, primarily by creating a comprehensive audit trail—a detailed digital log of every access attempt.
This data provides a powerful benefit. In the event of an incident, you have a precise, time-stamped record of every credential used, showing who it was and whether access was granted or denied. This eliminates guesswork and provides invaluable evidence for fast, accurate investigations. This detailed logging also simplifies regulatory compliance. Many industries require strict proof of who accessed sensitive areas, and a modern system can generate these reports with a few clicks, turning a stressful audit into a routine task.
Creating a Safer, More Responsive Environment
The ability to manage your facility in real-time is a game-changing benefit. During an emergency, you can trigger a facility-wide lockdown from a single dashboard, securing every access point instantly. This immediate response can be the critical factor in controlling a crisis.
The benefit extends beyond lockdowns. These systems provide a live overview of who is on-site. In an evacuation, this occupancy data is vital for first responders, helping them account for everyone and ensure no one is left behind.
The true peace of mind comes from knowing you can adapt to any situation instantly. Whether it's securing a single room or the entire campus, the control is in your hands, not determined by who has a physical key.
This responsive capability fundamentally enhances the protection of your people and property.
Achieving Tangible Operational Advantages
A significant benefit is the elimination of physical key management. The cost and security headache of re-keying an entire building due to a single lost key is a major vulnerability, and with an estimated 80% of businesses having dealt with this issue, it's a common one.
A modern access control system makes this problem disappear.
- Instant Revocation: Revoke access for a departing employee in seconds via software, rendering their old credential useless and eliminating the risk of unauthorized re-entry.
- Zero Re-keying Costs: Deactivate a lost card and issue a new one without the expense and time of calling a locksmith.
- Streamlined Onboarding: Grant new hires the exact access they need before their first day, making them productive immediately.
This control extends to non-employees. Integrating with a visitor management platform allows you to issue temporary, restricted access to guests that automatically expires. This ensures every person on-site is accounted for. You can explore more about the benefits of a visitor management system to see how these systems work together.
Ultimately, these systems provide a powerful return on investment by tightening security and making your entire operation more efficient and cost-effective.
Securing Your Entrance with Visitor Management
A top-tier physical access control system is excellent for employees, but what about guests, contractors, and other visitors? This constant flow of non-employees often represents a significant, unaddressed security gap. Relying on a paper sign-in sheet is like installing a state-of-the-art alarm but leaving the front door unlocked.
Integrating a dedicated visitor management system (VMS) with your access control platform provides a transformative benefit. This combination turns your reception area into an intelligent security checkpoint, creating a unified strategy that accounts for every person on your property. This approach fortifies your security posture, ensures a professional first impression, automates compliance, and frees your staff from manual work.
Moving Beyond the Paper Logbook
The traditional paper logbook is inefficient, insecure, and provides zero real-time insight. Information can be illegible, incomplete, or even falsified. A modern VMS solves these problems directly.
A recent study revealed that over 90% of organizations still rely on manual or partially automated visitor processes, leaving them exposed to security risks and inefficiencies. Integrating a VMS automates this workflow, ensuring every visitor is properly vetted and accounted for.
By digitizing the check-in process, you gain the benefit of a permanent, searchable, and accurate record of every visit. This digital trail is vital for compliance and provides a clear picture of who is on-site at any moment—a capability a paper logbook can never offer.
The Benefits of a Unified System
When your visitor management and access control systems communicate, you create a seamless and secure experience. This integration actively manages visitor access rights within your facility.
The core benefits include:
- Enhanced Security: Visitors receive temporary credentials that grant access only to pre-approved areas. Upon checkout, their access is automatically revoked, eliminating risk.
- Improved Compliance: A VMS automates policy enforcement, requiring visitors to sign NDAs or watch safety videos before their credentials are activated.
- Greater Operational Efficiency: The system handles pre-registration, host notifications, and badge printing, freeing your front desk team for more valuable tasks.
This integrated approach creates a more professional and secure first impression.
The advantages of an integrated approach become even clearer when you compare them.
Standalone vs Integrated Security Systems
This table highlights the enhanced security and efficiency gained when your visitor management and access control systems work as a single, cohesive unit.
| Feature | Standalone Access Control | Integrated System (PACS + VMS) |
|---|---|---|
| Visitor Tracking | No record of visitors, only credentialed employees. | Complete, auditable record of every person on-site. |
| Guest Access | Manual process; often requires a staff escort. | Automated issuance of temporary, restricted access credentials. |
| Compliance | Relies on manual checks and paperwork. | Automated enforcement of policies, NDAs, and safety briefs. |
| Emergency Response | Occupancy data is limited to employees only. | Provides a real-time list of all visitors and employees for accurate evacuation roll calls. |
The benefits go far beyond simple convenience.
Integrating these two systems creates a comprehensive security bubble around your facility, ensuring protocols apply to everyone, closing critical vulnerabilities, and building a safer, more efficient environment.
How to Choose Your Access control System

Choosing the right physical access control system is about finding a solution that fits your unique security needs, can grow with your business, and simplifies daily operations. Thoughtful planning ensures you get a system that provides long-term value.
Start by assessing your facility. The security needed for a busy lobby differs from that of a server room containing sensitive data. Identify your most critical assets and areas to understand what you need to protect.
Assess Your Specific Security Needs
Before looking at products, define your goals. Are you trying to prevent theft, protect intellectual property, ensure employee safety, or meet regulatory requirements? Your answer will guide your choices.
Ask yourself these questions:
- What are you protecting? Is it physical equipment, confidential data, or your people?
- Where are your high-risk areas? Identify server rooms, executive offices, or R&D labs requiring the strictest controls.
- Who needs access? Consider different groups like employees, managers, contractors, and visitors, each requiring different access levels.
A clear understanding of your risks helps you select a system with features that directly address them, preventing overspending on unnecessary features or underinvesting in critical security layers.
Prioritize Scalability and Future Growth
The system you choose today must accommodate your future needs. If you plan to grow from 50 to 500 employees, a system designed for a small office will quickly become obsolete. Scalability is essential to protect your initial investment.
A truly scalable system allows you to add more doors, users, and even new locations without a complete overhaul. This flexibility ensures your security keeps pace with your business.
Consider your five-year plan. Will you open new branches or need to secure more areas? A scalable system, especially a cloud-based one, provides the agility to handle these changes seamlessly, making security a partner in your growth, not an obstacle.
Evaluate Integration Capabilities
Your physical access control system gains power when it connects with other business tools. An integrated environment allows information to flow seamlessly, creating a smarter security ecosystem.
The most common integration is with video surveillance, allowing you to visually verify access events. Just as important is linking it with a visitor management platform. For a deep dive, see our guide on how to choose the right visitor management system for your business. This ensures every person on-site is accounted for. To fully cover your bases, you might also explore innovative lock solutions for enhanced protection that complement your digital system.
Consider User Experience and Compliance
The best security system is one that people use correctly. If a system is difficult to operate, employees may resort to security shortcuts like propping doors open. Modern systems with convenient credentials, such as mobile access, encourage proper use and enhance overall security.
At the same time, compliance with regulations like HIPAA or PCI-DSS is non-negotiable. Your system must be able to generate the detailed audit logs and access reports necessary to prove compliance. As security threats evolve, many organizations are shifting from traditional keycards to biometrics, while cloud integration enables real-time monitoring and predictive analytics.
Common Questions About Access Control Systems
Adopting a modern physical access control system is a significant step for any organization. It's a major investment that naturally raises questions. Here are clear, straightforward answers to the most common inquiries.
How Much Does a Physical Access Control System Cost?
The cost of an access control system varies significantly based on scale and complexity. A small business securing a single door might spend a few thousand dollars on essential hardware like a reader, an electric lock, and a basic controller. Conversely, a large corporate campus with hundreds of doors, advanced biometric scanners, and complex software integrations can see costs rise well into six figures.
Key cost drivers include:
- Number of Access Points: More doors, gates, or turnstiles require more hardware and installation.
- Credential Technology: Simple proximity cards are the most budget-friendly. Biometric readers for fingerprints or facial recognition represent a larger upfront investment.
- Software and Licensing: Software may involve a one-time fee or a recurring subscription, which is common for cloud-based solutions.
- Installation and Labor: Professional installation is crucial for security and functionality. Complex wiring increases this cost.
Rather than viewing it as an expense, consider access control a strategic investment. The cost of preventing a single theft or data breach—with the average breach now costing $4.45 million—can easily justify the initial outlay. Proactive security is simply smart business.
Can I Upgrade from a Traditional Lock and Key System?
Yes, upgrading from mechanical locks is the most common path to modernizing security. The process involves replacing standard lock hardware with electrified versions, such as electric strikes or magnetic locks (maglocks). These are then wired to an access reader and a central control panel.
The immediate benefits are significant. You eliminate the major vulnerabilities of physical keys.
- No More Re-keying: A lost key is no longer a crisis. Instead of the costly hassle of changing locks, you simply deactivate the lost credential in the software.
- Full Audit Trail: Every access attempt is logged, providing a complete record of who went where and when. This is invaluable for investigations and compliance.
- Remote Management: Gain the ability to grant or revoke access from anywhere, offering a level of control and flexibility that keys cannot match.
What Is the Difference Between On-Premise and Cloud-Based Systems?
The main difference lies in where your system's data and management software are located. The choice depends on your IT resources, security policies, and budget preferences.
An on-premise system houses all components—servers, software, and data—at your physical location. This offers direct control but requires your IT team to manage all maintenance, updates, and security.
A cloud-based system, or Access Control as a Service (ACaaS), hosts the management software with a third-party provider. This model reduces upfront hardware costs and offloads maintenance, updates, and security to the provider. A key benefit is the ability to manage your system securely from any device, anywhere.
How Does a Visitor System Truly Improve Security?
While a physical access control system is great for employees, it often has a blind spot: visitors. A visitor management system (VMS) is designed to close this critical security gap.
When integrated with access control, a VMS becomes the gatekeeper for every guest. The benefit is a fully automated visitor journey, from pre-registration to issuing temporary credentials with specific, time-limited access.
For example, a contractor can be granted access only to the server room between 9 AM and 5 PM on a specific day. Once they check out or the time expires, their access is instantly and automatically revoked. This simple but powerful feature ensures no one overstays their welcome or accesses unauthorized areas.
By integrating the two, you gain the benefit of a complete, auditable record of every person in your building, not just employees. It ensures no one slips through the cracks, elevating your security from good to exceptional. For more information, check out our comprehensive visitor management system FAQs.
Ready to close your security gaps and create a seamless, professional experience for everyone who walks through your doors? At VisitUs, we provide a powerful, integrated solution that secures your facility from the front desk to the factory floor. Discover how VisitUs can elevate your security and operational efficiency.