A Guide to Physical Access Controls
Physical access controls are the systems and strategies businesses use to manage who can enter a specific area. More than just a lock, these controls act as an intelligent gatekeeper, actively securing your spaces, people, and assets by preventing unauthorised entry. A staggering 60% of data breaches are caused by insiders, including former employees. Modern access controls tackle this risk by letting you instantly revoke access, ensuring that once an employee leaves, their ability to enter is immediately cut off.
Understanding Your First Line of Defence

Think of physical access controls like the security for your online bank account, but for your real-world locations. Your password and two-factor authentication protect your digital funds; in the same way, access controls protect your physical property. The core benefit is simple: you gain the power to grant access to the right people and deny it to everyone else.
This is a huge leap forward from the old lock-and-key method. A lost key is a permanent security risk until the lock is changed, with no way of knowing if it has been copied. Modern systems, however, provide dynamic control. Understanding the purpose of physical security safeguards is crucial because it shifts your mindset from simply locking a door to actively managing your entire environment.
More Than Just Stopping Intruders
The benefits of a modern physical access control system go far beyond keeping the wrong people out. They offer peace of mind and create operational advantages that can directly impact your bottom line.
A well-implemented system means you know exactly who is on-site at all times. This real-time visibility is crucial not just for security, but also for safety and compliance, especially during an emergency. It transforms security from a passive background thought into an active management tool that enhances operational efficiency.
By providing a complete audit trail of who accessed which areas and when, you gain invaluable data for incident investigations and compliance audits, turning security into a source of business intelligence.
Comparing Old and New Security Methods
The move from basic locks to intelligent, networked systems marks a major shift in how businesses protect themselves. Upgrading delivers granular control, detailed oversight, and a much safer environment for everyone. For a deeper look at other fundamental security elements, you might check out a comprehensive resource like the ultimate guide to bollards, which explains another key component in physical defence.
To really see the difference, it helps to put the old and new methods side-by-side.
Traditional vs Modern Physical Access Controls
| Feature | Traditional Controls (e.g., Lock & Key) | Modern Controls (e.g., Biometrics, VMS) |
|---|---|---|
| Audit Trail | None. No record of who enters or when. | Complete. Provides a detailed digital log of all access events. |
| Access Management | Manual. Requires physically changing locks. | Instant. Allows for remote and immediate granting or revoking of access. |
| Security Risk | High. Keys can be easily lost, stolen, or copied. | Low. Credentials are secure and difficult to duplicate. |
| Visitor Tracking | Inefficient. Relies on paper logbooks. | Streamlined. Offers real-time visibility and a professional welcome. |
As you can see, the upgrade isn't just a minor improvement—it’s a fundamental change in how you manage the safety and security of your premises.
Why Australian Businesses Are Upgrading Security
The need for robust physical access controls in Australia is a core business necessity. Companies across the country are moving past the outdated lock-and-key model due to a combination of growing security threats, rapid urbanisation, and the integration of smart technology. This isn't just about reacting to problems; it's a strategic move to protect valuable assets and create a safer environment.
Investing in modern security is no longer a line item you can push to next year's budget. It’s now a fundamental part of building a resilient business. The benefits are clear, offering not just better protection but also smoother operations and genuine peace of mind. By adopting intelligent systems, businesses can get ahead of risks instead of just responding to them.
The Accelerating Growth of the Security Market
The market's explosive growth illustrates this shift. The Australian physical security market, which includes physical access controls, is booming. Valued at roughly USD 68.7 billion in 2025, it’s projected to reach USD 121.3 billion by 2031. This massive jump shows how seriously organisations are taking the need for comprehensive security to protect their people, property, and critical infrastructure.
This growth is driven by the integration of advanced technology like biometrics and IoT-enabled monitoring. Businesses gain access to more powerful tools to prevent theft and vandalism while simplifying compliance and daily workflows.
The infographic below breaks down the main forces pushing this security upgrade across Australian businesses.
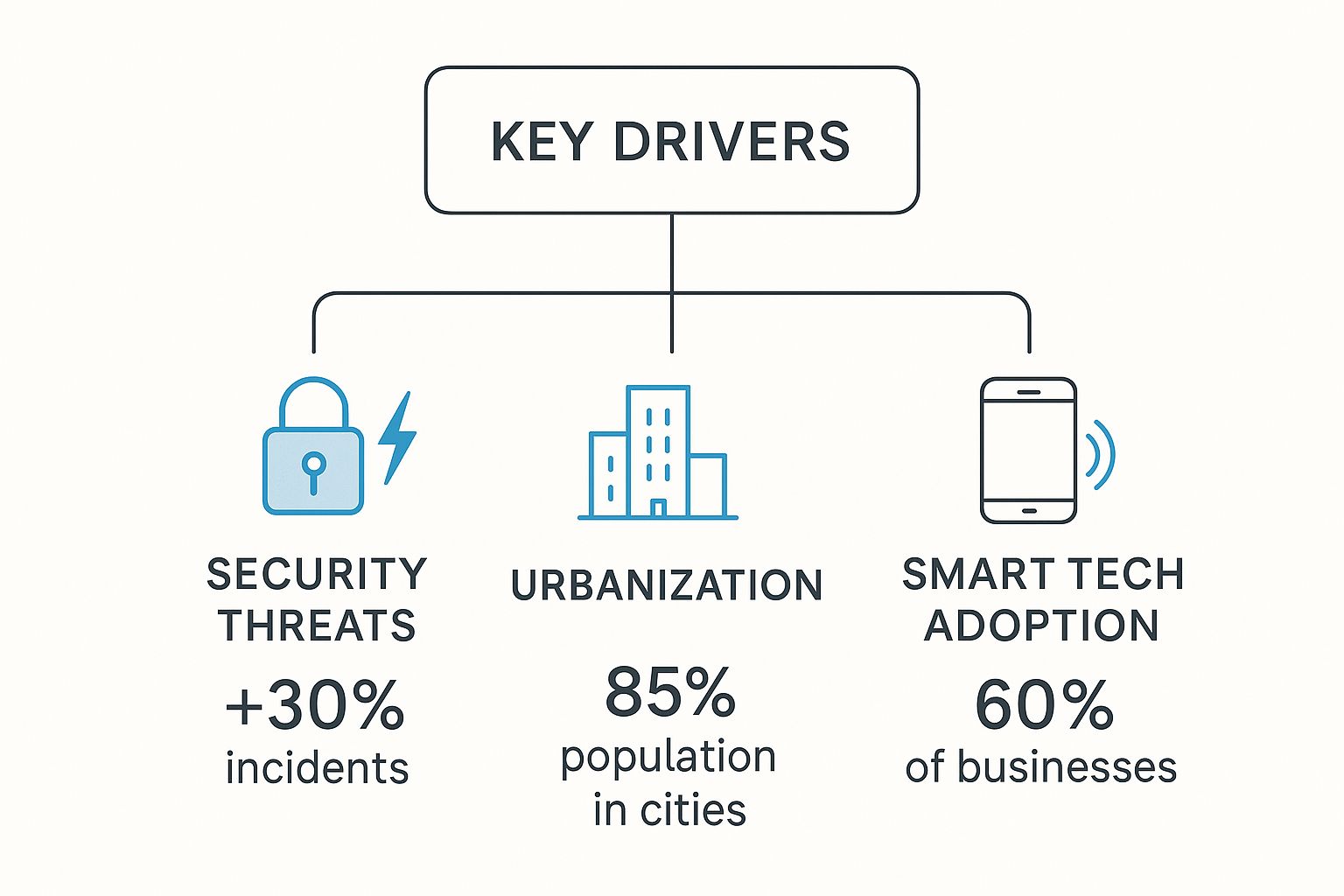
As the data shows, it's a perfect storm of rising security incidents, denser city populations, and new technology that's compelling businesses to modernise how they think about security.
Key Drivers for Enhanced Security
Several interconnected reasons explain why Australian companies are strengthening their physical access controls. Understanding these drivers makes it clear why a modern security posture is essential.
- Increasing Security Threats: As physical security incidents rise, a robust access control system acts as a crucial first line of defence, preventing unauthorised individuals from causing damage.
- Rapid Urbanisation: With most of the population in cities, commercial buildings are busier and more complex. Intelligent systems are needed to manage the flow of employees, visitors, and contractors efficiently.
- Adoption of Smart Technology: As businesses embrace digital tools, their physical security must keep pace. Modern systems integrate with other software, creating a unified and easy-to-manage security ecosystem. For a deeper dive, check out our guide to modern security for office spaces.
Ultimately, upgrading physical access controls is about gaining control and visibility. Modern solutions empower businesses to not only react to incidents but to proactively prevent them, ensuring compliance and protecting their most valuable assets.
Choosing Your Ideal Access Control System

Selecting the right physical access controls comes down to matching technology to your specific security needs. Every system strikes a different balance between security, convenience, and oversight. By understanding the benefits of each, you can make an informed choice that significantly strengthens your organisation's security.
The goal isn't just to lock doors; it's to gain real control and visibility over who goes where, and when. The right system provides invaluable data that improves operational efficiency and emergency preparedness. As you weigh the options, it helps to understand what the pros do. For a great overview, check out these 8 Essential Access Control Best Practices to help guide your thinking.
Card-Based Systems for Detailed Audit Trails
One of the most popular types of physical access controls relies on key cards, fobs, or smartphones. The primary benefit of these systems is the complete, digital audit trail they create. Every time a card is used, the system logs the user, location, and exact time.
This data provides immense value. If equipment goes missing, you can pull a detailed report to see exactly who entered the area and when. This instantly narrows down investigations, transforming security from a passive fence into an active management tool. Furthermore, the ability to instantly deactivate a lost card eliminates security risks on the spot—a vast improvement over the cost and hassle of rekeying traditional locks.
Biometric Systems The Ultimate in Personal Security
For areas demanding the highest level of security, biometric access controls are the top choice. These systems use unique biological traits like fingerprints or facial features for verification. The key benefit is that biometrics cannot be lost, stolen, or shared.
A key card can be handed over and a PIN can be shared, but a fingerprint belongs to only one person. This eliminates problems like "buddy punching" and guarantees that only authorized personnel can enter highly sensitive areas like data centres or R&D labs.
Research reveals a significant security vulnerability: 24% of employees would sell their work credentials to an outsider. Biometric systems neutralize this threat by tying access directly to an individual, not something they carry.
What once seemed like science fiction is now an accessible and reliable security solution. Biometrics offer unparalleled peace of mind, ensuring your most critical assets are protected by verifying the person, not just a credential.
Keypads and Other Common Controls
Keypad systems, requiring a PIN for entry, offer a straightforward, keyless solution. Their main benefit is convenience, as there are no physical cards to distribute or track. They are a solid choice for low-to-medium security areas where easy access is a priority.
However, this convenience must be weighed against security risks, as PINs can be forgotten, shared, or observed. For this reason, many businesses combine keypads with another form of authentication, creating a stronger, multi-factor security layer. The best security setups often involve a mix of technologies, tailored to the specific needs of each area within your facility.
How Mobile and Cloud Access Is Changing the Game

The future of physical access control is in your pocket. The shift to mobile credentials, where a smartphone acts as a secure key, represents a massive leap forward for both security and operational efficiency. This is about more than convenience; it's about gaining real-time, dynamic control over your facilities.
Imagine giving a contractor access for just one day. Instead of managing a physical key card, you can issue a temporary digital pass directly to their phone, set to expire the moment the job is done. This instant, remote management is a game-changer for any organisation that juggles visitors, temporary staff, or a flexible workforce.
The Power of Cloud-Based Control
This flexibility is powered by the cloud. Managing your physical access controls through a central, cloud-based platform makes your entire security setup smarter and more responsive. You are no longer tied to an on-site server to make changes.
Administrators can grant, modify, or revoke access permissions instantly from anywhere with an internet connection. This is a significant benefit for businesses with multiple sites, allowing one manager to oversee facilities nationwide. It also eliminates the major costs and security risks associated with lost or stolen key cards. For a deeper look at this modern approach, see how a cloud-based visitor management system can work seamlessly with these controls.
The switch to mobile and cloud solutions isn't just a niche trend; it's quickly becoming the industry standard. This move prepares your business for the future, making sure your security measures are always up-to-date and ready to handle the latest threats.
Adopting the New Standard in Australia
Australian organisations are quickly realising the security and efficiency benefits of mobile and cloud-based systems. Industry analysis shows that 37% of security leaders in Australia and globally have already implemented mobile credentials, with another 32% planning to adopt them soon. This data highlights the rapid shift away from legacy systems toward integrated platforms that future-proof security.
This transition delivers standout benefits for modern workplaces:
- Enhanced Security: Mobile credentials use encryption and multi-factor authentication, making them far more secure than traditional key cards.
- Greater Convenience: People are less likely to forget their smartphone than an ID badge, reducing lockouts and administrative burdens.
- Operational Efficiency: Centralised management drastically reduces the time your team spends on administrative tasks like issuing cards or changing access levels.
By embracing mobile and cloud technology, you aren’t just upgrading your locks—you’re investing in a more secure, agile, and efficient way to manage your physical spaces.
Securing High-Value Assets and Infrastructure
When protecting high-value locations like data centres, research labs, or sensitive government facilities, a simple lock is insufficient. These modern-day fortresses house critical assets and confidential data, demanding a smarter, layered approach to physical access controls. The goal is not just to lock the front door but to build multiple layers of security that work together.
This 'defence in depth' strategy can be pictured like a medieval castle. An attacker would face a moat, an outer wall, an inner wall, and guards at every gate. Each layer is designed to deter and expose threats. In modern security, this means combining different types of physical access controls to create an overlapping security net.
Building an Impenetrable Defence
A truly secure facility integrates several technologies, each with a specific role. The perimeter might be secured with fences and video surveillance. Building entry could require a key card, while access to the most sensitive areas, like a server room, would demand a biometric scan.
The primary benefit of this multi-layered system is the elimination of single points of failure. If one security measure is bypassed, others are in place to stop an intruder. This integrated defence ensures only the right people can get near your most critical assets.
The Data Centre Example
Australian data centres exemplify this principle. As the digital vaults of our economy, they store vast amounts of sensitive information, driving huge investment in sophisticated security.
The Australian data centre physical security market, valued at USD 81 million in 2024, is projected to more than double to USD 176 million by 2029. This boom is a direct response to the need for integrated video surveillance, biometric scanners, and other advanced controls to safeguard our digital lives. You can dive deeper into this trend and discover key insights into the Australian data centre security market.
The real power of a multi-layered system is that it allows for proactive threat management. By weaving together video feeds, biometric data, and access logs, security teams can spot suspicious patterns and stop potential incidents before they escalate, rather than just cleaning up the mess after a breach.
The Role of AI in Advanced Security
Artificial intelligence is taking this defensive strategy to a new level. AI-powered analytics can monitor numerous security feeds simultaneously, detecting anomalies a human operator might miss, such as a stolen key card being used or an attempt to 'tailgate' an employee through a secure door.
This benefit shifts security from being reactive to proactive. Instead of reviewing footage after an incident, AI helps identify and neutralize threats in real time. For anyone responsible for protecting high-value assets, this capability provides an unprecedented level of peace of mind.
Elevating Security with a Visitor Management System
While employees may have secure credentials, visitors, contractors, and couriers often represent a significant, and frequently overlooked, gap in a physical access control strategy.
A paper logbook is an outdated method that offers no real-time visibility or genuine security. A modern visitor management system (VMS) bridges this gap by becoming the central command for every non-employee on your site. The benefit is transforming a clunky, manual process into a secure, smooth, and professional welcome. Instead of a messy sign-in sheet, guests use a simple, digital check-in that captures all crucial information, creating a complete digital audit trail. This turns a potential security vulnerability into a significant strength.
Gaining Real-Time Visibility and Control
Integrating a VMS with your physical access controls provides immediate insight into who is on your premises at any given moment. With a startling 79% of organisations believing they could be breached by a third party like a contractor, the need for better oversight is clear. A VMS delivers that clarity.
In an emergency evacuation, a VMS provides an instant, accurate list of every visitor and contractor on-site, accessible from any device. This is not just about security; it’s about ensuring the safety and well-being of every person in your building.
This real-time data benefits your security team by enabling them to:
- Instantly spot unauthorised individuals by comparing the on-site list with access control logs.
- Account for everyone during an emergency, leading to a faster, more organised response.
- Monitor contractor movements to ensure they adhere to designated work areas.
Streamlining Compliance and Professionalism
A VMS automates compliance with health and safety regulations. The system ensures every visitor acknowledges safety policies, signs NDAs, or completes necessary health screenings before entry. This creates a benefit for your business by removing manual compliance burdens and creating a complete, auditable record.
It also creates a seamless, professional first impression. Visitors can often pre-register online and receive a QR code for a quick, touchless check-in. This not only speeds things up but also demonstrates that your organisation takes security and efficiency seriously, setting a positive tone from the moment they arrive. The benefits of a dedicated visitor management system for offices extend beyond security, fostering a welcoming and well-organised environment.
A VMS turns compliance from a tedious administrative chore into a smooth, integrated part of the visitor journey. It ensures every legal and safety box is ticked without creating friction for your guests, all while building a detailed, auditable record.
The Modern Visitor Journey
Here's how an integrated VMS enhances the visitor experience:
- Pre-Registration: The visitor receives an email invitation and completes their registration online, which can include signing an NDA.
- Arrival and Check-In: Upon arrival, they scan a QR code at a kiosk, which instantly verifies their identity and prints a visitor badge.
- Host Notification: Their host receives an automatic notification that their guest has arrived.
- Controlled Access: The visitor’s badge can be programmed to grant temporary access only to specific areas for the duration of their visit.
- Secure Check-Out: As they leave, they check out at the kiosk, and their access credentials are automatically deactivated.
This entire flow is secure and efficient, proving that robust security and a great visitor experience can go hand in hand.
Got Questions About Physical Access Controls?
It's normal to have questions when considering a security upgrade. Moving to a modern physical access control system is a significant step, and understanding the practical details is key to making a confident decision. Let's address some common questions.
A frequent concern is the disruption of switching from an old lock-and-key setup. The benefit of modern systems is a streamlined installation process. Professionals can often retrofit new electronic locks and readers onto existing doors, minimizing disruption to your daily operations.
Another question is about cost. While there's an upfront investment, the long-term savings are compelling. A recent survey showed that businesses without automated security can lose thousands annually from internal theft alone. By preventing such incidents, a good access control system can quickly pay for itself.
Can Small Businesses Really Benefit from Access Control?
Absolutely. Physical access controls are no longer just for large corporations. Scalable, cloud-based solutions have made this level of security accessible and affordable for businesses of any size.
For a small business owner, the ability to manage access remotely from a phone is a game-changer. This provides significant peace of mind by protecting inventory, equipment, and sensitive customer data—assets that are as vital to a small business as they are to a global one.
How Does Access Control Handle Power Outages?
This is a critical safety question. Professional physical access control systems are designed with failsafe mechanisms. Most electronic locks can be configured as either "fail-safe" (unlocking automatically for emergency exit) or "fail-secure" (remaining locked to maintain security), depending on the door's purpose.
Additionally, many systems include battery backups to maintain operation during a power cut. This is a key concern for 9 out of 10 facility managers, and this feature ensures your site remains secure and accessible even when the lights go out.
What Happens If Someone Loses a Key Card?
Unlike a traditional metal key, a lost key card is a minor issue. An administrator can instantly deactivate the lost card from the central management system in seconds, rendering it useless.
The benefit is that you completely avoid the significant cost and hassle of rekeying all your locks. You can simply issue a new card to the employee, ensuring they can get back to work without disruption while your building remains secure.
Ready to enhance your security and streamline your front desk operations? VisitUs provides a secure, cloud-based visitor management system that integrates seamlessly with your physical access controls, ensuring every person on-site is accounted for. Discover how our system can deliver greater efficiency, safety, and insight by exploring our solutions.